Published
- 10 min read
SPIFFE and SPIRE Explained: The Foundation of Zero Trust for Machines (Part 1)
In the traditional era of on-premise data centers, security was relatively simple: we built a castle wall (the firewall) and assumed everything inside was safe. Applications were identified by their IP addresses, which rarely changed.
But the cloud-native revolution broke this model. In Kubernetes and multi-cloud environments, IP addresses are ephemeral. Workloads scale up and down in seconds. Containers die and are reborn with new identities. Relying on network location for security is no longer viable.
Worse, we fell into the trap of “Secrets Management.” To let Service A talk to Database B, we issue an API Key. But how do we deliver that key to Service A? We inject it. But how does Service A authenticate to get that injection? With another secret. This is the “Secret Zero” problem it’s “turtles all the way down.” We are drowning in a sea of static, long-lived credentials that are a nightmare to rotate and a goldmine for attackers.
Enter SPIFFE and SPIRE. These two projects are revolutionizing machine identity by moving us from “secret-based” security to “property-based” Zero Trust.
This is Part 1 of our deep-dive series. Today, we are stripping away the complexity to explain exactly what these concepts are, the mechanics of attestation, and why they are becoming the industry standard for workload identity.
What to Remember
- SPIFFE vs. SPIRE: SPIFFE is the standard (the “rules”), SPIRE is the software implementation (the “infrastructure”).
- Property-Based Identity: Identities are issued based on what the software is (kernel PID, container image, namespace), not a password it holds.
- The SVID: This is the digital passport (usually an X.509 certificate) that proves a workload’s identity for mTLS.
- Secret Zero Solved: By using platform attestation (verifying the node and process properties), SPIRE eliminates the need to inject a master secret to start the chain of trust.
- Short-Lived Credentials: SVIDs are rotated automatically and frequently (e.g., every hour), significantly reducing the impact of credential theft.
1. What is SPIFFE?
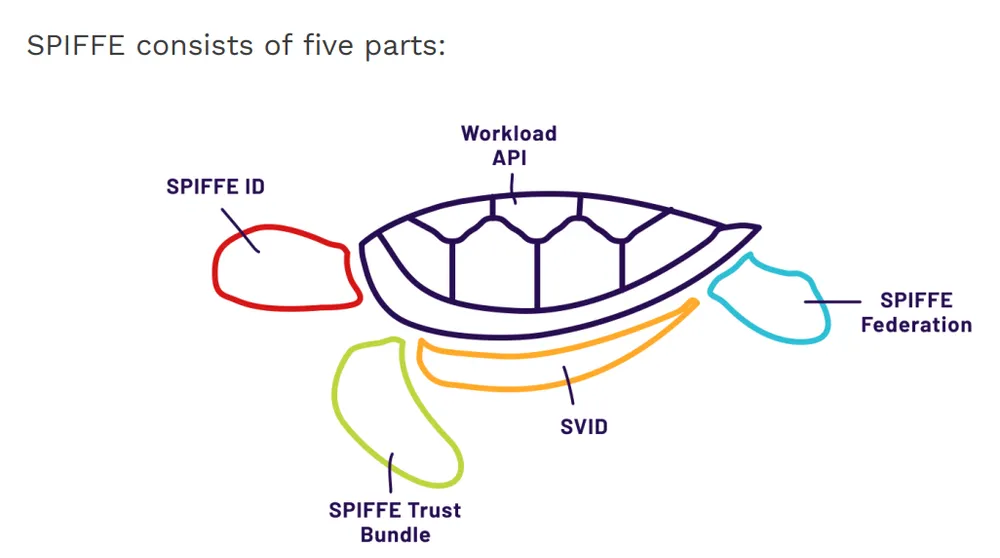
SPIFFE stands for Secure Production Identity Framework For Everyone. It is an open-source standard, hosted by the Cloud Native Computing Foundation (CNCF), that defines a universal way for software services (workloads) to identify themselves to each other across different environments, clouds, and platforms.
Think of SPIFFE not as software, but as the Passport Convention (like the ISO standards that dictate what a physical passport looks like). It doesn’t print the passport, but it defines the rules.
The Three Core Pillars of SPIFFE
-
SPIFFE ID (The Name): A standardized string that uniquely identifies a workload. It looks like a URI.
- Format:
spiffe://<trust-domain>/<workload-identifier> - Example:
spiffe://acme.com/billing-service - This ID is platform-agnostic. It doesn’t care if the service is running on AWS EC2, a Raspberry Pi, or a Kubernetes Pod.
- Format:
-
SVID (The ID Card): The SPIFFE Verifiable Identity Document. This is the actual credential that contains the SPIFFE ID. It allows the workload to prove its identity to others.
- X.509 SVID: A standard X.509 certificate used primarily for establishing mTLS (Mutual TLS) connections.
- JWT SVID: A JSON Web Token used for asserting identity to verifiers (like checking into a cloud provider’s IAM).
-
The Workload API (The Distribution Method): This is the most critical part. The Workload API is a local, standardized API (usually a Unix Domain Socket) exposed on the node.
- Workloads call this API to say, “Who am I?”
- The API responds with the workload’s SVID and private key.
- Crucially: The workload does not need to authenticate to call this API. The system authenticates the workload (we will explain how in the SPIRE section).
-
SPIFFE Federation (Cross-Domain Trust): In the real world, organizations don’t operate in isolation. Your services might need to communicate with a partner’s services, or across different business units with separate trust domains.
- Federation allows two or more Trust Domains to establish mutual trust.
- Example:
spiffe://acme.comcan be configured to trust workloads fromspiffe://partner.io. - This enables secure cross-organizational or cross-cloud communication without sharing private keys.
- How it works: Domains exchange their Trust Bundles (public keys). When a workload from
partner.iopresents an SVID, services inacme.comcan verify it using the federated bundle.
-
SPIFFE Trust Bundle (The Root of Trust): The Trust Bundle is the foundational element that makes verification possible. It is essentially a collection of root CA certificates for a Trust Domain.
- Every Trust Domain has its own Trust Bundle containing the public keys used to sign SVIDs.
- Workloads use the Trust Bundle to verify that an SVID was legitimately issued by a trusted authority.
- Think of it as the “list of approved passport authorities.” When you see a passport, you check if the issuing country is on your trusted list.
- Automatic Distribution: The Workload API provides not just the SVID, but also the Trust Bundle, ensuring workloads always have up-to-date verification material.
2. What is SPIRE?
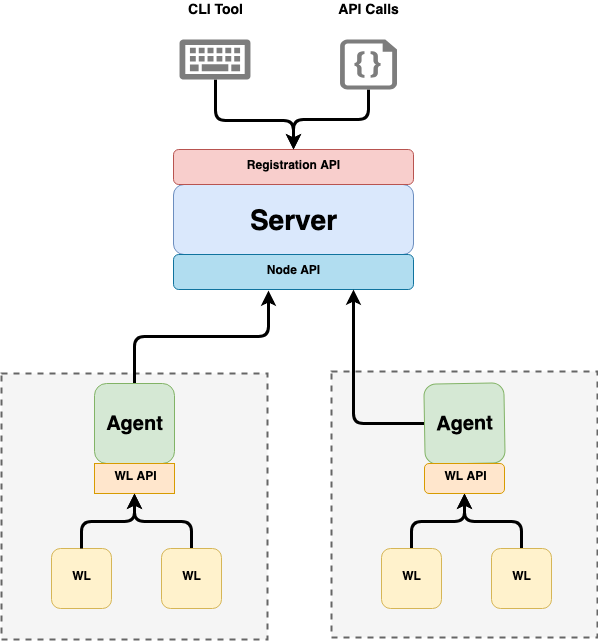
If SPIFFE is the law, SPIRE (SPIFFE Runtime Environment) is the infrastructure that enforces it. It is the production-ready software implementation that issues, manages, and rotates these identities.
SPIRE solves the operational complexity of PKI (Public Key Infrastructure). Instead of a security team manually generating certificates, SPIRE automates the issuance of short-lived credentials based on the attributes of the software running.
The Architecture of SPIRE
SPIRE is composed of two main components that communicate constantly:
A. The SPIRE Server
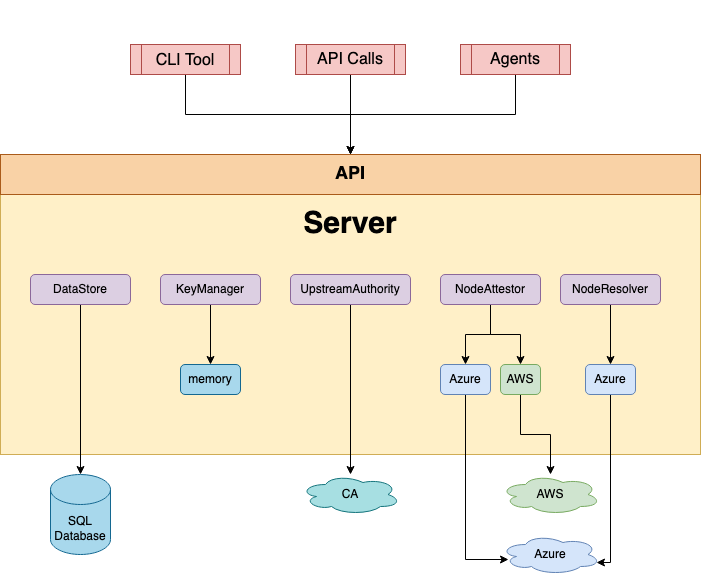
The Server is the central certificate authority (CA) for your Trust Domain.
- It manages the Registration Entries (a database of which workloads are allowed to run and what SPIFFE IDs they get).
- It signs the SVIDs for the Agents.
- It manages the root keys and federation with other domains.
B. The SPIRE Agent
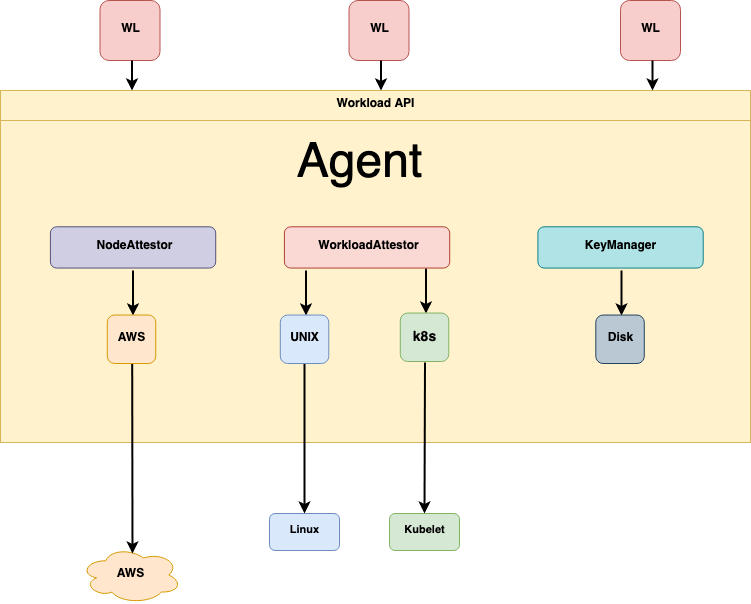
The Agent is a lightweight daemon installed on every node (VM, Physical Server, or K8s Node) in your cluster.
- It exposes the Workload API to the services running on that node.
- It performs Attestation (verifying the workload’s properties).
- It fetches SVIDs from the Server and caches them locally for the workloads.
3. The Magic of Attestation: Solving “Secret Zero”
This is the technical heart of SPIRE and what separates it from a standard Vault or Secret Manager. How does SPIRE give a certificate to a workload without the workload presenting a password first?
It uses a process called Attestation. Instead of checking what you know (a password), it checks what you are (your properties).
Phase 1: Node Attestation
Before the Agent can issue IDs, the SPIRE Server must trust the machine the Agent is running on.
- When the SPIRE Agent starts, it gathers proof of the underlying infrastructure.
- Example on AWS: It pulls the Instance Identity Document (IID) signed by AWS.
- Example on Kubernetes: It uses the Kubernetes Service Account Token.
- The Agent sends this proof to the Server. The Server verifies the AWS signature. If valid, the Server issues an identity to the Agent itself.
Phase 2: Workload Attestation
Now a workload (e.g., a Docker container) starts up and requests an identity.
- The Workload connects to the SPIRE Agent’s socket.
- The Agent asks the Operating System kernel: “Who is on the other end of this connection?”
- The Kernel provides process details: PID (Process ID), User ID, Cgroups.
- The Agent uses Workload Attestors to inspect the process further:
- Kubernetes Attestor: Looks at the Kubelet to see which Pod, Namespace, and Service Account matches that PID.
- Docker Attestor: Looks at the Docker Daemon to see the Image ID, Labels, and Env Vars.
- If these properties match a Registration Entry defined in the Server, the Agent issues the SVID.
Result: You have authenticated the software based on its verified attributes (Namespace, Image SHA, etc.) without injecting a single static secret.
4. Vulgarized Explanation: The High-Security Facility
To visualize how this works, let’s leave the cloud and imagine a high-security research facility.
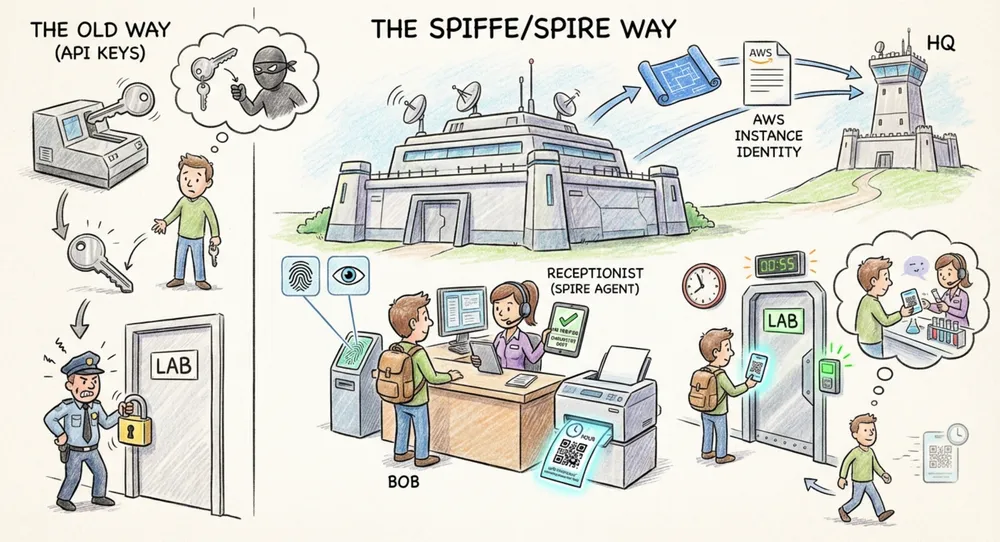
The Scenario: You have employees (Microservices) who need to enter specific labs (Databases).
The Old Way (API Keys): You give every employee a metal key.
- Risk: Keys can be copied. If an employee gets fired, you have to change the locks. If an employee loses a key, anyone who finds it can enter the lab.
The SPIFFE/SPIRE Way:
-
The Building (The Node): The facility itself is verified. Before the doors open, the building sends its architectural blueprints and government permits (AWS Instance Identity) to HQ. HQ confirms this is a sanctioned building.
-
The Receptionist (The SPIRE Agent): A new researcher, Bob, walks in. He has no badge. He walks up to the Receptionist.
- Secret Zero: Bob doesn’t say a password.
- Attestation: The Receptionist scans Bob’s retina, checks his fingerprints, and verifies with HR that “Bob is scheduled to work in the Chemistry Department today.” This relies on inherent traits (Bio-metrics/Kernel PID), not secrets.
-
The Badge (The SVID): The Receptionist confirms Bob is legitimate. They print a digital badge.
- Crucial Detail: This badge is valid for only 1 hour.
- Content: The badge says
spiffe://facility/chemistry/researcher-bob.
-
Access (mTLS): Bob walks to the Lab door. The door reader cryptographically verifies the badge. It confirms it was signed by HQ and hasn’t expired. The door opens.
-
Rotation (Lifecycle): 55 minutes later, while Bob is working, the Receptionist silently walks over and hands him a new badge valid for the next hour. Bob doesn’t stop working. If Bob is fired (Workload deleted), the Receptionist stops issuing badges. The old badge expires in minutes, and access is cut off automatically.
Conclusion: The New Identity Standard
SPIFFE and SPIRE fundamentally change the security landscape. They allow us to move away from IP-based perimeter security (which fails in the cloud) and static-secret management (which fails at scale).
By assigning dynamic, short-lived, and cryptographically verifiable identities to every piece of software, we build a foundation for true Zero Trust.
But what does this look like in the real world? Is it actually better than managing IAM roles? In the next part of this series, we will explore the concrete benefits and real-world use cases, comparing SPIFFE/SPIRE to traditional IAM and looking at how giants like Uber and Netflix leverage this technology.
To further enhance your cloud security and implement Zero Trust, contact me on LinkedIn Profile or [email protected]
Next: Read Part 2: Benefits, Examples, and Use Cases →
Frequently Asked Questions (FAQ)
What is the main difference between SPIFFE and SPIRE?
SPIFFE is the open standard (the "rules") that defines how workloads should identify themselves. SPIRE is the software implementation (the "tool") that distributes and manages these identities in production.
Does SPIRE replace OAuth or OIDC?
Not necessarily. SPIRE excels at backend service-to-service authentication (machine identity), usually via mTLS. OAuth/OIDC are often used for user authentication. However, SPIRE can issue JWTs that are compatible with OIDC flows.
What is the "Secret Zero" problem?
The "Secret Zero" problem is the challenge of how to securely introduce the very first secret (like an API key) to an application so it can access other secrets. SPIRE solves this by using platform attestation instead of a pre-shared secret.
Do I need Kubernetes to use SPIRE?
No. While SPIRE is very popular in Kubernetes, it works on bare metal, VMs (AWS EC2, Google Compute Engine), and hybrid environments. It is platform-agnostic.
What happens if the SPIRE Agent goes down?
If the Agent fails, workloads on that node cannot renew their SVIDs. Once the short-lived SVIDs expire, the workloads will lose access to other services, effectively failing securely (fail-closed).
