Published
- 7 min read
Shai-Hulud 2.0: The Recursive Nightmare Eating the Software Supply Chain
In Frank Herbert’s Dune, Shai-Hulud is the giant sandworm, a force of nature that consumes everything in its path. In late 2025, the cybersecurity world is facing a digital manifestation of this beast. Shai-Hulud 2.0 is not just another vulnerability; it is a self-propagating contagion that has evolved beyond the tactics of its predecessor. Unlike traditional attacks that target a specific vulnerability, this campaign weaponizes trust itself, turning your own developers and CI/CD pipelines into unwitting distributors of malware.
If you thought the SolarWinds or Log4j incidents were the peak of supply chain anxiety, Shai-Hulud 2.0 is here to reset the baseline. With over 25,000+ malicious repos across ~350 GitHub users including major banks, government agencies, and tech giants already impacted, the question is no longer “if” you are exposed, but “how deep” the worm has burrowed. This blog explores the mechanics of this devastating campaign, revisits the fundamentals of supply chain risks, and provides the immediate steps you must take to survive the fallout.
What to Remember
- It’s a Worm: Unlike static malicious packages, Shai-Hulud 2.0 is recursive. It infects a developer’s machine, steals their publishing credentials, and automatically publishes malware-laden versions of their legitimate packages.
- Trust is the Vector: The attack succeeds because the malware comes from trusted, highly reputable maintainers whose accounts have been compromised without their knowledge.
- Cross-Ecosystem Threat: While initially focused on NPM, the 2.0 wave has aggressively expanded to PyPI, threatening both JavaScript and Python ecosystems.
- The Kill Chain: The malware focuses on exfiltrating environment variables (secrets, API keys) and spreading further. It is an identity theft engine.
Back to Basics: The Supply Chain Vulnerability Concept
To understand the gravity of Shai-Hulud 2.0, we must strip away the jargon and look at the modern software factory. Today, no one writes code from scratch. We build applications like Lego structures, using thousands of third-party blocks (libraries, packages, dependencies) hosted on public registries like NPM (Node.js) or PyPI (Python).
A Supply Chain Attack occurs when an adversary infiltrates your system not by breaking down your front door, but by poisoning one of the bricks you use to build it.
- Traditional Attack: Hacker attacks your server.
- Supply Chain Attack: Hacker compromises a library you trust (e.g.,
lodashorrequests). You download the update, thinking it is a security patch, but you are actually installing a backdoor.
The danger lies in implicit trust. We assume that if a package comes from a known author, it is safe. Shai-Hulud 2.0 exploits exactly this assumption by compromising the author, not the code.
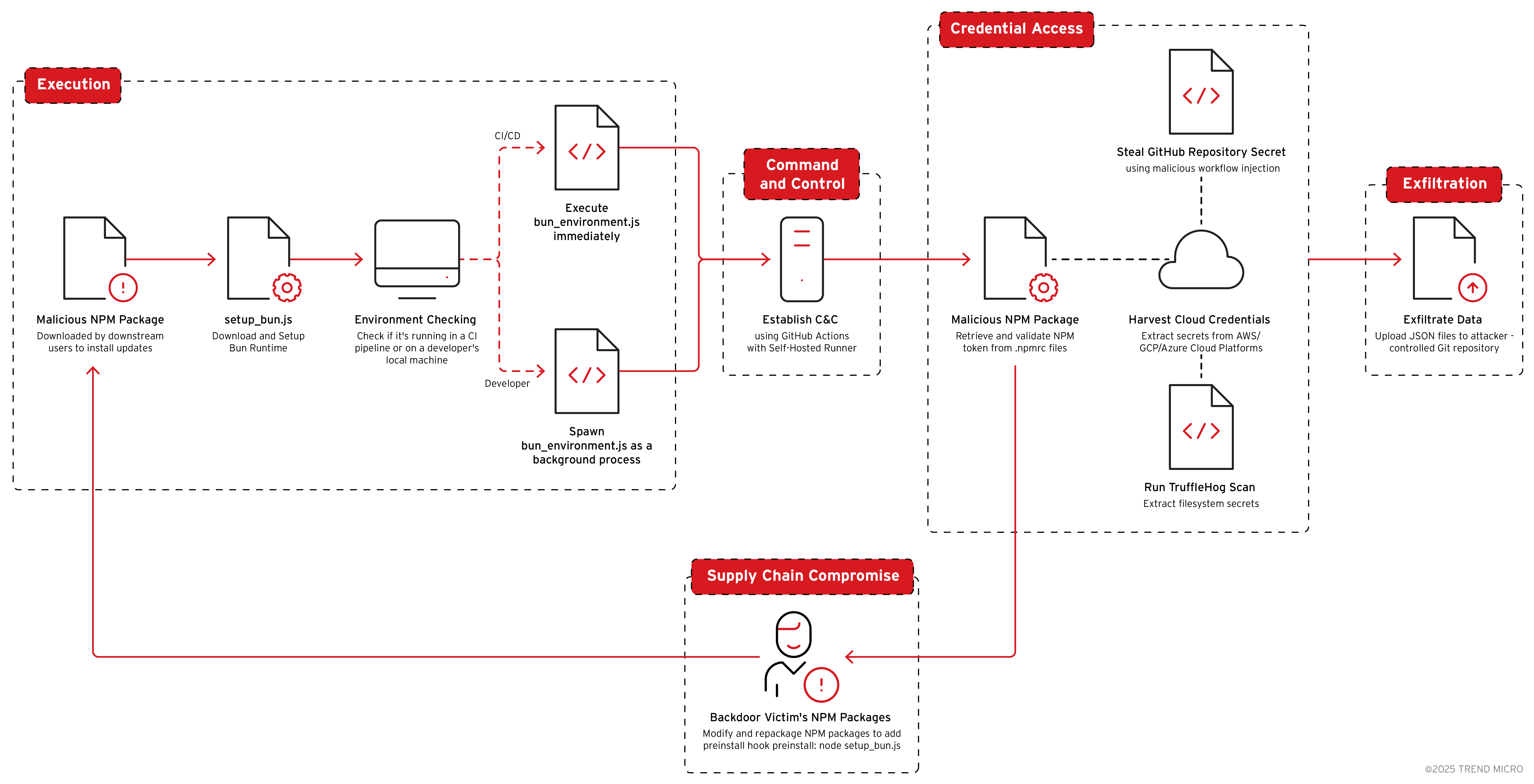
The Mechanism: Anatomy of a Recursive Attack
What makes Shai-Hulud 2.0 distinct and terrifying is its recursive nature. It operates like a biological virus.
- Patient Zero: An attacker publishes a useful-looking package containing a malicious
postinstallscript. - Infection: A developer installs this package. The script executes immediately on their local machine or CI server.
- Credential Theft: The script scans the environment for authentication tokens (specifically
.npmrcfiles,~/.pypirc, or environment variables likeNPM_TOKENandPYPI_API_TOKEN). - Propagation (The Worm): This is the game-changer. The malware doesn’t just steal the token; it uses it. It queries the registry to list all other packages owned by that developer. It then automatically publishes new patch versions of those legitimate packages, injecting its own malicious code into them.
- Exponential Spread: Everyone who trusts that developer and updates their dependencies gets infected. The cycle repeats instantly.
This automated propagation allows the attack to move laterally across organizations and vertically through dependency trees at machine speed.
The Impact: 25,000+ Malicious Repos Across ~350 GitHub Users
The scale of Shai-Hulud 2.0 is staggering. Reports from Wiz and Datadog indicate that the second wave has hit over 25,000+ malicious repos across ~350 GitHub users.
- Sector Agnostic: The victims range from Fortune 500 banks to critical government infrastructure providers.
- Data Exfiltration: Beyond spreading, the malware exfiltrates sensitive environment variables to Command and Control (C2) servers. This means AWS keys, database credentials, and API secrets are being harvested en masse.
- Reputational Damage: Open-source maintainers are finding their reputations destroyed overnight as their accounts are used to attack their own user base.
What to Check
Detecting Shai-Hulud 2.0 requires moving beyond standard vulnerability scanning (CVEs). You are looking for behavioral anomalies and specific Indicators of Compromise (IoCs).
- Audit Recent Updates: Check your dependency tree for packages that have been updated in the last 72 hours, especially “patch” updates (e.g., 1.0.1 to 1.0.2) from authors who rarely update.
- Inspect
postinstallScripts: The malware relies heavily onpostinstallscripts inpackage.json(NPM) orsetup.py(PyPI). Look for obfuscated code or scripts that execute network requests (curl/wget) to unknown domains. - Check for “Stealth” Dependencies: The malware often adds a dependency to the manifest that looks similar to a popular package (typosquatting) or uses a dependency that has been recently taken over.
- Review Network Traffic: Monitor your CI/CD and developer environments for unexpected outbound traffic to known C2 domains associated with the campaign (refer to threat intel feeds from Wiz/Datadog).
Remediation
If you suspect exposure, immediate containment is critical.
- Check impacted dependencies: in this list : https://github.com/wiz-sec-public/wiz-research-iocs/blob/main/reports/shai-hulud-2-packages.csv.
- Rotate All Credentials: Assume your CI/CD environment variables and developer tokens are compromised. Revoke NPM tokens, PyPI API keys, AWS Access Keys, and GitHub Personal Access Tokens immediately.
- Pin Dependencies: Stop the bleeding by pinning your dependencies to the last known “good” hash (using
package-lock.jsonorpoetry.lock). Do not allow “floating” versions (e.g.,^1.0.0).
Conclusion: The New Normal of Trust
Shai-Hulud 2.0 teaches us a harsh lesson: in the software supply chain, you are only as secure as the least secure developer in your dependency tree. The era of blindly running npm install or pip install is over. To survive, organizations must treat external code as untrusted by default, inspecting not just the vulnerability database, but the behavior and provenance of the software itself. The worm is out there, and it is hungry for your credentials.
To further enhance your cloud security and implement Zero Trust, contact me on LinkedIn Profile or [email protected]
Frequently Asked Questions (FAQ)
What is Shai-Hulud 2.0?
Shai-Hulud 2.0 is a massive, recursive software supply chain attack. It functions as a worm that infects developer environments, steals publishing credentials, and automatically releases malicious versions of legitimate software packages to spread further.
Why is it called a "recursive" attack?
It is recursive because it uses the victim to create more victims. Instead of just infecting one machine, it uses the infected developer's identity to compromise all the software packages they maintain, thereby infecting everyone who uses those packages.
How do I know if I am infected?
Check for unexpected outbound network connections from your build servers, look for unauthorized releases of your own internal or public packages, and audit your package.json or requirements.txt for recently updated dependencies containing suspicious postinstall scripts.
Does this affect only NPM?
No. While the first wave focused on NPM (JavaScript), Shai-Hulud 2.0 has aggressively expanded to include PyPI (Python), making it a cross-ecosystem threat.
Who is responsible for stopping this?
It is a shared responsibility. Package registries (NPM/PyPI) are working to remove malicious packages, but organizations must implement "Software Composition Analysis" (SCA) and strict credential management to protect their own pipelines.
Resources
- Wiz Research: Shai-Hulud 2.0 Aftermath & Ongoing Attack
- The Hacker News: Second Wave Affects 25,000 Organizations
- Datadog Security Labs: Analysis of the Shai-Hulud 2.0 NPM Worm
- PyPI Blog: PyPI Response to Shai-Hulud Campaign
- Entro Security: Impact on Banks and Gov Tech
