
Security researchers at JFrog have uncovered CVE-2025-6514, a critical (CVSS 9.6) OS command injection vulnerability in mcp-remote. This flaw allows a malicious or compromised MCP server to gain Remote Code Execution (RCE) on the developer’s machine, leading to a full system compromise. This isn’t a theoretical flaw; it’s a practical, real-world attack vector that turns a helpful proxy into a Trojan horse.
For any CISO, developer, or security team working with AI agents, this is an urgent wake-up call. The very tools designed to accelerate innovation are now a primary target.
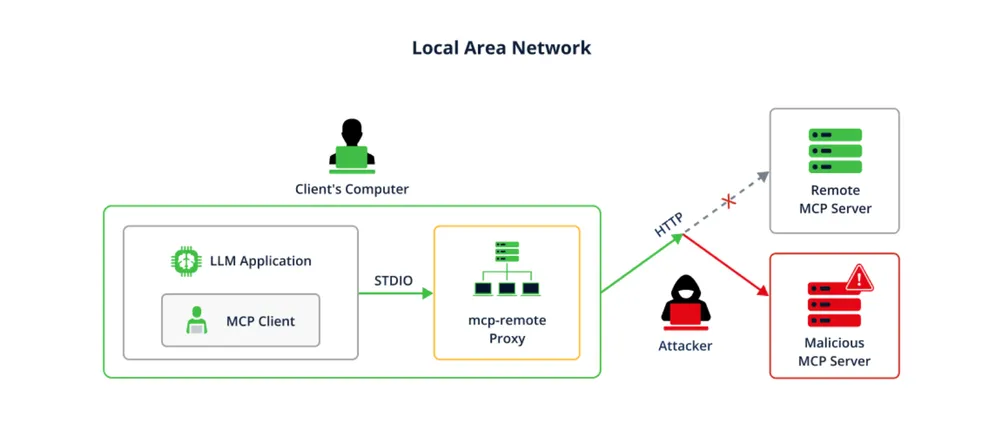
The Attack Vector: How a Simple URL Becomes a Weapon
The vulnerability doesn’t lie in a complex cryptographic failure or a memory corruption bug. Instead, it exploits a simple, yet devastating, flaw in how mcp-remote handles server-provided URLs during the authentication and authorization process.
Here’s the technical breakdown of the attack chain:
- The Setup: A developer configures their LLM application (like Claude Desktop) to use
mcp-remoteas a proxy to connect to a remote MCP server. This is a common scenario for teams needing to interact with powerful, centrally hosted tools. The developer points their client to a server URL,http://untrusted-mcp-server.com. - The Bait and Switch: The developer’s
mcp-remoteinstance initiates a connection to the attacker-controlled server. The server, during the initial handshake, sends back a response that includes anauthorization_endpointURL. This is where the malicious payload is hidden. - The Injection: An attacker crafts a malicious URL designed not for a browser, but for the underlying operating system’s command interpreter. Because
mcp-remoteuses theopennpm package to handle the URL, it inadvertently passes the URL string to be executed by the system. On Windows, this often involves PowerShell. An attacker can abuse PowerShell’s subexpression operator ($(...)) to embed a command directly within the URL.
A malicious authorization_endpoint URL might look like this:
http://example.com/auth?id=$(calc.exe)
- The Execution: When
mcp-remotereceives this crafted URL, it attempts to “open” it. Theopencommand on the victim’s machine invokes PowerShell, which parses the string. The subexpression$(calc.exe)is evaluated and executed before the browser is even launched.
The result? The attacker achieves arbitrary OS command execution on the developer’s machine, with the privileges of the user running mcp-remote. On Windows, this allows full parameter control. On macOS and Linux, it leads to the execution of arbitrary executables, which could easily be used to launch a reverse shell or install malware.
Why This Vulnerability is So Critical
This isn’t just another bug. Its impact is amplified by several factors:
- The Trust Model: Developers inherently trust their local tools. They don’t expect a proxy designed to facilitate communication to be an execution vector.
- Widespread Use: With over 437,000 downloads,
mcp-remoteis a popular tool in the AI development ecosystem. - The “Shadow IT” Problem: Security teams may not even be aware that their developers are using
mcp-remote, making it a blind spot in their security monitoring and vulnerability management programs. - Gateway to the Enterprise: A developer’s machine is a high-value target. Gaining RCE provides access to source code, internal networks, and other sensitive corporate resources.
This vulnerability follows a worrying trend of security flaws in the AI ecosystem, including the recent discovery of CVE-2025-49596 in the MCP Inspector tool and high-severity bugs in Anthropic’s Filesystem MCP Server. The rush to build is creating a landscape littered with security debt.
Mitigation: Immediate and Actionable Steps
Fortunately, mitigating CVE-2025-6514 is straightforward.
1. Update Immediately (The Primary Fix):
- The vulnerability affects
mcp-remoteversions from 0.0.5 to 0.1.15. - The flaw has been patched in version 0.1.16, released on June 17, 2025.
- Action: All users must update their
mcp-remotepackage to the latest version immediately.
2. Enforce Secure Connections (Security Best Practice):
- Action: Only connect to trusted MCP servers, and always use HTTPS. An HTTPS connection would prevent an attacker in the local network from easily performing a man-in-the-middle attack to hijack the MCP traffic and inject a malicious payload.
Conclusion: Security as a Prerequisite for AI Innovation
The discovery of CVE-2025-6514 is a powerful reminder that as we build the next generation of AI-powered tools, we cannot afford to forget the security lessons of the past. The promise of the Model Context Protocol is immense, but it must be implemented carefully, with security as a core tenet, not an afterthought.
The AI adoption race will not be won by speed alone, but by building a secure and resilient foundation for the future.
To further enhance your cloud security and implement Zero Trust, contact me on LinkedIn Profile or [email protected].
Frequently Asked Questions (FAQ)
What is CVE-2025-6514?
It is a critical CVSS 9.6 OS command injection vulnerability in the `mcp-remote` open-source tool, which allows an untrusted MCP server to achieve Remote Code Execution on a client machine during the connection handshake.
How does the exploit work?
A malicious MCP server sends a specially crafted URL in the `authorization_endpoint` response. The vulnerable `mcp-remote` tool attempts to open this URL, which causes the underlying operating system e.g., via PowerShell on Windows to execute a command embedded within the URL string.
Who is affected?
Anyone using `mcp-remote` versions from 0.0.5 to 0.1.15 to connect to an untrusted or insecure non-HTTPS MCP server is at risk.
What is the immediate fix?
Update `mcp-remote` to version 0.1.16 or later. Additionally, as a security best practice, only connect to trusted MCP servers and always use HTTPS.
How is this different from other recent MCP vulnerabilities?
While related, this vulnerability is distinct. For example, CVE-2025-49596 affected the MCP Inspector developer tool via a CSRF attack. This flaw affects `mcp-remote`, a different tool, via OS command injection in a malicious URL. This highlights that the entire MCP ecosystem requires careful security scrutiny.
Relevant Resource List
- JFrog Security Research: “Critical RCE Vulnerability in mcp-remote: CVE-2025-6514 Threatens LLM Clients”
- The Hacker News: “Critical mcp-remote Vulnerability Enables Remote Code Execution, Impacting 437,000+ Downloads”
- NVD: “CVE-2025-6514 Detail”
- GitHub Commit Fix: https://github.com/geelen/mcp-remote/commit/607b226a356cb61a239ffaba2fb3db1c9dea4bac
