For years, companies protected their networks like castles with strong outer walls (firewalls) and a trusted inside. But times have changed. With cloud computing, remote work, and apps spread across the internet, that clear boundary no longer exists. Your data can now be anywhere, accessed by anyone, on any device.
Relying on the old perimeter-based approach is no longer enough. That’s where Zero Trust comes in. It’s not just a buzzword it’s a necessary shift in how we think about security today.
While moving to Zero Trust can seem overwhelming, it doesn’t have to be. This guide will explain what Zero Trust really means, lay out a step-by-step plan, and show you how to implement it effectively on Google Cloud Platform (GCP).
What is Zero Trust, Really? Beyond the Buzzword
At its core, Zero Trust operates on a single, powerful principle articulated by Google as part of its Well-Architected Framework: “Never trust, always verify.”
This model shifts the security focus from protecting a “trusted” network to protecting the resources themselves. It assumes there is no implicit trust granted to any user, device, or workload based on its physical or network location. Whether a request originates from inside a corporate office or from a coffee shop halfway across the world, it is treated with the same initial level of skepticism.
Implementing a Zero Trust model means embracing a few core practices:
- Eliminating Implicit Trust: There are no more “trusted” internal networks. Every access request must be validated.
- Enforcing Least Privilege: Grant users and services only the minimum level of access required to perform their specific tasks, for the shortest time necessary.
- Explicitly Verifying Every Access Request: Rigorously authenticate and authorize every user, device, and service before granting access to resources. This validation should be dynamic, considering contextual signals like user identity, device posture, location, and more.
- Assuming Breach: Consciously operate and defend your assets with the assumption that an adversary is already inside your environment. This mindset drives continuous verification and security posture monitoring.
The benefits are significant: a drastically reduced attack surface, minimized impact from potential breaches, a better and more seamless user experience (goodbye, clunky VPNs), and a security posture prepared for the realities of modern IT.
The Roadmap to Zero Trust: A Phased, Strategic Journey
Zero Trust is not a single product you can buy and deploy overnight. It’s a strategic journey that involves a combination of people, processes, and technology. While the complete roadmap can consist of dozens of comprehensive projects, making early progress is key to building momentum.
A vendor-agnostic Zero Trust architecture can be broken down into key components or pillars of organizational security. You can start your journey with a few high-impact, low-effort projects that deliver immediate benefits.
Five Simple Projects to Kickstart Your Zero Trust Adoption:
- Enforce Multi-Factor Authentication (MFA) for Critical Applications: Credential theft via phishing remains a top attack vector. MFA is the single best protection. Instead of a full, immediate rollout, start by enforcing MFA on your most critical applications. This is an impactful first win.
- Implement Zero Trust Policy Enforcement for Critical Applications: Go beyond just verifying identity. Apply granular access policies to your critical apps that consider a variety of behavioral and contextual factors before authenticating, and then continuously monitor that activity.
- Monitor Email and Filter Phishing Attempts: Email is the number one entry point for attackers. Apply Zero Trust principles by enhancing email security beyond standard filters. Consider using technologies like remote browser isolation (RBI) to quarantine suspicious links, effectively neutralizing threats before they can execute.
- Close All Inbound Ports Open to the Internet: Open inbound network ports are a massive attack vector. Instead of exposing applications directly, use a Zero Trust reverse proxy (like an application load balancer with an identity service) to securely expose web applications to the public internet without opening any inbound ports on your firewall. The application’s only publicly visible record becomes its DNS entry, which can also be protected.
- Block DNS Requests to Known Threats or Risky Destinations: DNS filtering is a simple yet powerful way to prevent users from accessing malicious websites or C2 (command-and-control) servers. By blocking these requests at the DNS level, you can prevent many threats from ever reaching your endpoints.
By completing these five projects, your organization will have made significant progress toward a more modern and resilient security posture, creating a solid foundation for the broader Zero Trust journey.
Implementing Zero Trust on Google Cloud: A Practical Blueprint
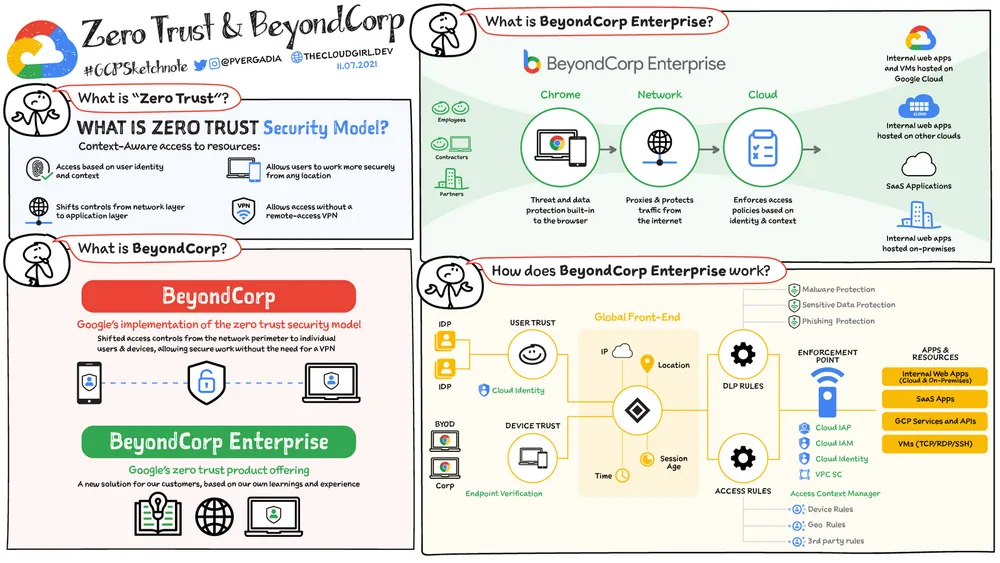
Google has been on its own decade-long Zero Trust journey since the “Operation Aurora” attacks in 2009, leading to the creation of its BeyondCorp model. As a result, GCP is inherently designed to support Zero Trust principles, providing a rich toolkit of services that map directly to the NIST 800-207 Zero Trust framework.
Here’s how you can implement the core tenants of Zero Trust using GCP services:
1. Verify Explicitly: Strong, Context-Aware Identity and Access
Principle: Don’t trust any user or device. Rigorously authenticate and authorize every access attempt based on dynamic context.
GCP Toolkit:
- Cloud Identity: Acts as your central Identity Provider (IdP), supporting federation with existing IdPs like Active Directory or Azure AD for seamless Single Sign-On (SSO).
- Multi-Factor Authentication (MFA): GCP supports various MFA methods, including Titan Security Keys for phishing-resistant authentication.
- Identity-Aware Proxy (IAP): This is a core component. IAP acts as a policy enforcement point, verifying user identity and device context before granting access to web applications or VMs. It shifts access control from the network perimeter to individual users and devices.
- BeyondCorp Enterprise: Google’s premium Zero Trust solution provides rich device-level signals (e.g., OS version, screen lock, encryption status) via Endpoint Verification, allowing for highly granular, context-aware access decisions.
2. Enforce Least Privilege: Granting Minimal, Necessary Access
Principle: Minimize the risk of unauthorized access and lateral movement by granting only the permissions needed to perform a task.
GCP Toolkit:
- IAM (Identity and Access Management): Use granular, predefined IAM roles instead of overly permissive primitive roles (Owner, Editor, Viewer). Create custom roles when necessary.
- IAM Conditions & Just-in-Time (JIT) Access: Grant temporary, time-bound access to resources, which automatically expires.
- Workload Identity Federation: Allows workloads running outside of GCP (e.g., on-premises or in another cloud) to securely access GCP resources without needing service account keys.
- Service Accounts: Treat service accounts as privileged identities. Grant them minimal roles and strictly control who can impersonate them (
iam.serviceAccounts.actAs).
3. Secure the Network: From Perimeter to Microsegmentation
Principle: Assume the network is hostile. Protect resources and prevent data exfiltration by segmenting networks and inspecting all traffic.
GCP Toolkit:
- VPC Service Controls: Create secure perimeters around sensitive data and services to prevent data exfiltration. This is a powerful tool against insider threats and compromised credentials.
- Google Cloud Armor: Provides Web Application Firewall (WAF) and DDoS protection at the network edge, protecting applications from common web threats.
- Cloud IDS & Cloud NGFW: Monitor for malicious network activity with intrusion detection and prevention services.
- Private Service Connect: Securely access Google Cloud services and APIs without exposing traffic to the public internet.
- VPC Network Design: Use Virtual Private Clouds (VPCs) and firewall policies to logically isolate workloads and control traffic flow between them.
4. Assume Breach: Comprehensive Monitoring and Automation
Principle: Continuously monitor all activity to detect and respond to threats quickly, assuming an attacker is already inside.
GCP Toolkit:
- Cloud Logging & Monitoring: Provides centralized, real-time visibility into all activity across your GCP environment.
- Security Command Center (Premium): Your central hub for security posture management. It automatically scans for vulnerabilities and misconfigurations, detects threats, and provides actionable insights.
- Chronicle (SIEM & SOAR): Google’s security operations suite allows you to correlate security events from various sources at petabyte scale, hunt for threats, and automate incident response.
- Infrastructure as Code (IaC): Use tools like Terraform and Cloud Build to automate infrastructure provisioning, ensuring consistent and secure configurations.
Conclusion: Your Journey to a More Secure Future Starts Now
Transitioning to a Zero Trust architecture is no longer a question of if, but how. It’s a strategic imperative for any organization serious about protecting its data, applications, and users in a perimeter-less world. While the journey may seem complex, it can be broken down into a logical, phased roadmap.
By starting with high-impact projects like enforcing MFA and closing open inbound ports, organizations can build early momentum. And by leveraging the powerful, integrated services within Google Cloud from IAP and BeyondCorp to Cloud Armor and Security Command Center you have a robust toolkit at your disposal to turn the principles of Zero Trust into a practical reality. The time to challenge implicit trust and build a more resilient security foundation is now.
To further enhance your cloud security and implement Zero Trust, contact me on LinkedIn Profile or [email protected].
Zero Trust on GCP FAQ:
Frequently Asked Questions (FAQ)
What is Zero Trust in simple terms?
Zero Trust is a security model based on the principle of "never trust, always verify." It eliminates the idea of a trusted internal network and requires every access request to be rigorously authenticated and authorized before granting access to a resource, regardless of where the request originates.
Is Zero Trust only for cloud environments?
No, Zero Trust principles can and should be applied across hybrid environments, including on-premises data centers, remote users, and multiple clouds. The goal is to provide consistent security policy enforcement everywhere.
What is the most important first step in a Zero Trust journey?
While it varies by organization, enforcing Multi-Factor Authentication MFA on all users, especially for critical applications, is widely considered one of the most impactful and crucial first steps. It immediately mitigates the risk of credential theft.
How does Google Cloud's security model differ from a traditional network?
Google Cloud's model is built on Zero Trust principles. Services like Identity-Aware Proxy IAP shift access controls from the network perimeter to individual user and device identities. VPC Service Controls create perimeters around data and services, rather than just the network. This provides more granular and context-aware security.
Can I implement Zero Trust in phases?
Absolutely. In fact, a phased approach is highly recommended. Start with a few high-impact projects like the five listed in this article to build momentum and demonstrate value. The full Zero Trust journey is a marathon, not a sprint.
Relevant Resource List:
- Google Cloud Whitepaper: “Applying Zero Trust on Google Cloud” (Mapping GCP services to NIST 800-207)
- Google Cloud Well-Architected Framework - Security Pillar: “Implement zero trust”
- Cloudflare Blog: “Roadmap to Zero Trust” (For the 5 simple projects concept)
- A Roadmap to Zero Trust Architecture: (Vendor-agnostic roadmap from zerotrustroadmap.org)
- NIST Special Publication 800-207: “Zero Trust Architecture” (The foundational guiding document for Zero Trust)
