
The ground has shifted beneath our feet once again. For cybersecurity professionals, the release of a new OWASP Top 10 is more than just an update; it’s a recalibration of our focus and a reflection of the evolving digital threat landscape. The Open Web Application Security Project (OWASP) has unveiled its 2025 list, and the message is unequivocally clear: the perimeter has dissolved, and the fight has moved deep into our code and supply chains. This isn’t just another checklist; it’s a critical intelligence briefing for developers, CISOs, and security architects on the most pressing application security risks today. Understanding these risks is essential for building a zero trust architecture that extends to your applications.
The 2025 edition brings two significant new categories into the fold and reshuffles the hierarchy of well-known threats, painting a vivid picture of a world grappling with interconnected, systemic vulnerabilities. Gone are the days when we could focus solely on isolated code flaws. Now, the integrity of our entire development lifecycle from the open-source libraries we import to how our applications behave under stress is under the microscope. This latest update is a direct response to the escalating complexity of modern software and the sophisticated attack vectors that have come to define our era.
What to Remember
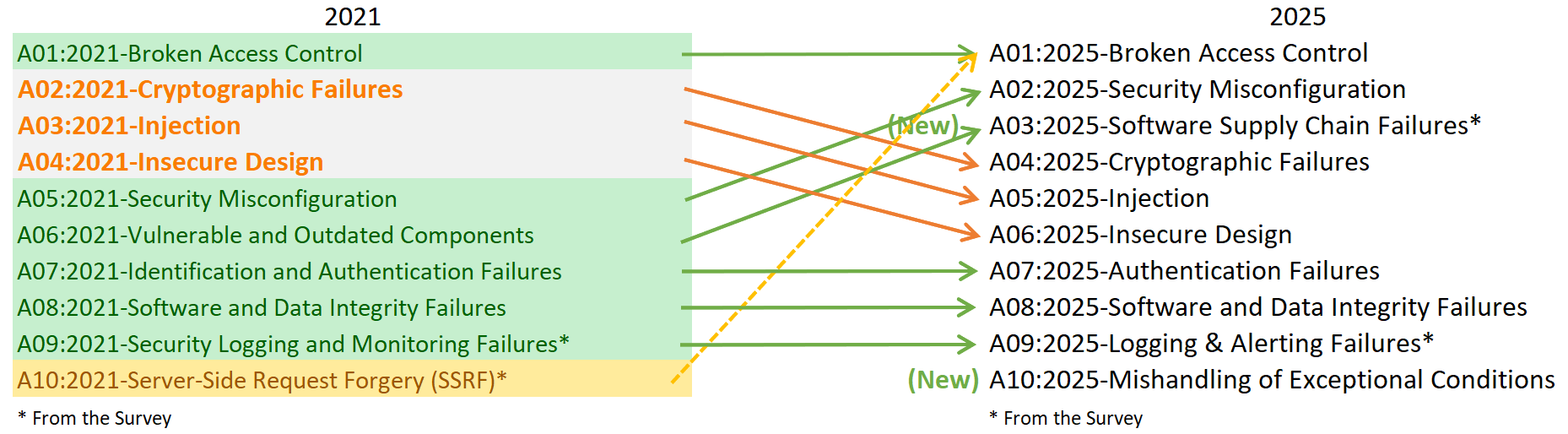
- Two Major New Risks: The list introduces “A03: Software Supply Chain Failures” and “A10: Mishandling of Exceptional Conditions,” signaling a major shift in focus.
- Supply Chain is the New Perimeter: The emphasis on supply chain failures acknowledges that modern applications are assembled, not just written, making dependency security paramount.
- Resilience Matters: How your application fails is now as important as how it operates. Secure error handling is no longer just “good code quality” but a top-tier security concern.
- The Basics Still Bite: “Broken Access Control” remains the number one risk, proving that mastering foundational security principles is more critical than ever.
A New Class of Threat: A03:2025 - Software Supply Chain Failures
Perhaps the most significant and timely addition to the OWASP Top 10 is “Software Supply Chain Failures,” which has landed squarely at number three. This category is an evolution of the previous “Vulnerable and Outdated Components,” but its scope is vastly broader and more reflective of today’s development realities. It acknowledges a stark truth: a single compromised dependency, a tampered build tool, or a malicious package in a public registry can cascade into a catastrophic breach across thousands of applications. This directly relates to broader supply chain security vulnerabilities that organizations must address.
The modern software supply chain is a complex web of dependencies, APIs, and third-party services. While this ecosystem accelerates innovation, it also creates an expansive attack surface. Attackers are no longer just knocking at the front door; they are poisoning the well. By injecting malicious code into widely used libraries or compromising build pipelines, adversaries can gain trusted access to the very heart of an application. This risk isn’t theoretical; well-publicized attacks like those on SolarWinds and Log4j have served as painful reminders of the potential for widespread damage.
Mitigating Software Supply Chain Failures requires a multi-layered defense:
- Software Bill of Materials (SBOM): You cannot secure what you cannot see. Maintaining a detailed and dynamic SBOM is the foundational step to understanding every component and dependency within your applications.
- Dependency Scanning: Integrate automated tools like Software Composition Analysis (SCA) into your CI/CD pipeline. These tools continuously scan for known vulnerabilities in your third-party packages, providing real-time alerts.
- Verifying Integrity: Whenever possible, verify the digital signatures and integrity of the packages you use. Utilize secure, private registries for storing and managing approved components, reducing the risk of typosquatting or dependency confusion attacks.
- Principle of Least Privilege for CI/CD: Your build and deployment pipelines are now critical infrastructure. Enforce strict access controls and monitor them for any signs of tampering or unauthorized activity.
When Systems Break: A10:2025 - Mishandling of Exceptional Conditions
The second newcomer, debuting at the tenth position, is “Mishandling of Exceptional Conditions.” This entirely new category highlights a subtle but critical aspect of application resilience: how a system behaves when things go wrong. For years, poor error handling was often dismissed as a quality issue, but OWASP now rightfully categorizes it as a significant security risk.
Exceptional conditions such as a lost database connection, a timeout from a microservice, or unexpected user input can push an application into an unstable state. If not handled securely, these states can lead to devastating consequences. Attackers can deliberately trigger errors to probe for weaknesses, hoping the application will “fail open” by granting unauthorized access, or that it will leak sensitive information through verbose error messages, like stack traces or database details.
Building resilient and secure applications means planning for failure:
- Fail Closed by Default: Your system’s default response to an error should be to deny access and maintain a secure state. Privilege-handling logic that fails open is a direct path to privilege escalation.
- Sanitize Error Messages: Never expose sensitive system information to the end-user. Generic, user-friendly error messages should be presented, while detailed error information is logged securely on the backend for developers to analyze.
- Structured Exception Handling: Implement a consistent and robust exception-handling strategy across your entire application. Unhandled exceptions can lead to denial-of-service conditions or reveal exploitable logical flaws.
- Threat Modeling for Failure States: During the design phase, actively threat model what happens when different components fail. This proactive approach helps identify potential security gaps before a single line of code is written.
The Shifting Landscape: Key Changes in the 2025 List
Beyond the new additions, the 2025 update reveals a significant reordering of priorities.
- A01: Broken Access Control Retains the Crown: For the second time in a row, Broken Access Control is the number one risk. This category, which involves flaws that let users bypass authorization and access data or functions they shouldn’t, remains the most common and critical finding in applications. Its persistence underscores the industry-wide challenge of correctly implementing complex authorization logic. Implementing the Principle of Least Privilege is essential to mitigating this risk. The 2025 list even expands this category by merging the former Server-Side Request Forgery (SSRF) risk into it, acknowledging that SSRF is often a means to bypass access controls.
- A02: Security Misconfiguration Surges: Jumping from fifth to second place, Security Misconfiguration highlights the growing complexity of modern application environments. As deployments increasingly rely on cloud services, containers, and intricate configurations, the potential for a simple mistake like an exposed storage bucket or a default password to create a major vulnerability has soared.
- Familiar Foes Slide But Remain Critical: Classic vulnerabilities like A04: Cryptographic Failures and A05: Injection have moved down the list but are far from gone. Their lower ranking may reflect better tooling and awareness, but a single injection flaw can still lead to a complete system compromise. These foundational risks demand continued vigilance.
Practical Implications for Security Teams and Developers
The OWASP Top 10 is not merely an academic document; it is a call to action. For CISOs, it provides a data-driven framework to guide security strategy and justify investments in key areas like DevSecOps and supply chain security. For developers, it serves as a practical guide for secure coding and a reminder that security is a shared responsibility throughout the entire software development lifecycle (SDLC).
Integrating the 2025 update into your security program should be a priority:
- Educate and Train: Host workshops and training sessions to familiarize your development and security teams with the new categories and the shifts in risk priority.
- Update Security Tooling: Ensure your SAST, DAST, and SCA tools are configured to detect the vulnerabilities outlined in the new list, with a particular focus on supply chain and configuration issues.
- Refine Threat Models: Update your threat modeling exercises to explicitly include scenarios related to supply chain compromises and exceptional condition handling.
- Embed Security in the SDLC: Continue to shift security left by integrating security checks, code reviews, and automated testing early and often in the development process. The goal is to make security a natural part of the workflow, not a bottleneck.
Conclusion: A New Standard for Cyber Resilience
The OWASP Top 10 2025 is a clear and concise reflection of the challenges we face in a highly interconnected and rapidly evolving digital world. It rightly pushes the conversation beyond traditional vulnerabilities towards the more systemic risks embedded in our software supply chains and the very resilience of our applications. By understanding and addressing these critical risks, we can move beyond a reactive security posture and begin to build a culture of proactive cyber resilience. The battlefield has changed, and with this new map from OWASP, we are better equipped to defend it.
Frequently Asked Questions (FAQ)
What is the OWASP Top 10 2025?
The OWASP Top 10 2025 is a globally recognized standard awareness document from the Open Web Application Security Project. It outlines the ten most critical security risks to web applications, based on comprehensive data and community feedback, to help organizations prioritize their security efforts.
Why did OWASP add Software Supply Chain Failures to the list?
OWASP added this category due to the dramatic increase in attacks targeting the software supply chain. Modern applications heavily rely on third-party and open-source components, and compromising a single component can impact thousands of organizations simultaneously, making it a highly critical risk.
How can developers prevent Mishandling of Exceptional Conditions?
Developers can prevent this by implementing robust, structured exception handling that fails "closed" by default, sanitizing all user-facing error messages to avoid leaking information, and threat modeling for potential failure states in the application's architecture.
When should my organization adopt the new OWASP Top 10 2025?
Organizations should begin aligning their security practices, tools, and training with the new list as soon as possible. The OWASP Top 10 reflects the current threat landscape, and early adoption ensures your application security program is focused on the most relevant and critical risks.
Who is responsible for implementing the OWASP Top 10 mitigations?
Application security is a shared responsibility. While developers are on the front lines of implementing secure coding practices, security teams are responsible for providing the right tools and guidance, architects must create secure designs, and leadership must foster a security-conscious culture.
Resources
- Official OWASP Top 10 2025: https://owasp.org/Top10/
- OWASP Software Assurance Maturity Model (SAMM): https://owaspsamm.org/
- OWASP Application Security Verification Standard (ASVS): A framework for testing application security controls.
- Threat Modeling Manifesto: Provides guiding principles for effective threat modeling.
- NIST Secure Software Development Framework (SSDF): A set of best practices for integrating security throughout the software development lifecycle.
