As a security leader, you face a relentless barrage of questions from the board, your peers, and your own teams. “Are we secure?” “Are we spending enough on cybersecurity?” “How do we compare to our competitors?” In the chaotic, high-stakes world of cyber risk, answering these questions with clarity and confidence is one of the most difficult parts of the job. We are drowning in a sea of vendor solutions, complex regulations, and thousands of daily alerts.
What we desperately need is a common language a way to organize the chaos, a blueprint to guide our strategy, and a tool to communicate risk in a language the business understands.
That tool is the NIST Cybersecurity Framework (CSF). Too often, the CSF is mistaken for just another compliance checklist to be ticked off and filed away. This is a profound misunderstanding of its power. The NIST CSF is not a rigid set of rules; it is a strategic framework for managing cybersecurity risk. When wielded correctly, it can transform your security program from a reactive cost center into a resilient, business-aligned function. This is your guide to moving beyond the checklist and mastering the CSF as a CISO.
What is the NIST CSF (And What It Isn’t)?
Created by the U.S. National Institute of Standards and Technology, the Cybersecurity Framework was born from a need to create a voluntary, common language for cybersecurity risk management. It was designed to be adaptable to any organization, regardless of size, industry, or cybersecurity maturity.
What the NIST CSF is:
- A Framework for Organization: It provides a structured way to think about and manage all aspects of your cybersecurity program.
- A Communication Tool: It creates a common vocabulary that allows technical teams, CISOs, and non-technical executives to talk about cybersecurity risk in a consistent way.
- A Strategic Blueprint: It helps you assess your current security posture, define your desired future state, and build an actionable roadmap to get there.
- A “Rosetta Stone”: It maps its controls to other major standards and frameworks like ISO 27001, COBIT, and CIS Controls, allowing you to harmonize your compliance efforts.
What the NIST CSF is not:
- It is not a mandatory standard (unless you are a U.S. federal agency or are required by contract).
- It is not a certification. You cannot be “NIST CSF certified.”
- It is not a one-size-fits-all set of prescriptive controls. It tells you what you should be able to do, but not how you must do it.
Deconstructing the Framework: The Three Core Components
To master the CSF, you need to understand its three main parts: the Core, the Tiers, and the Profile.
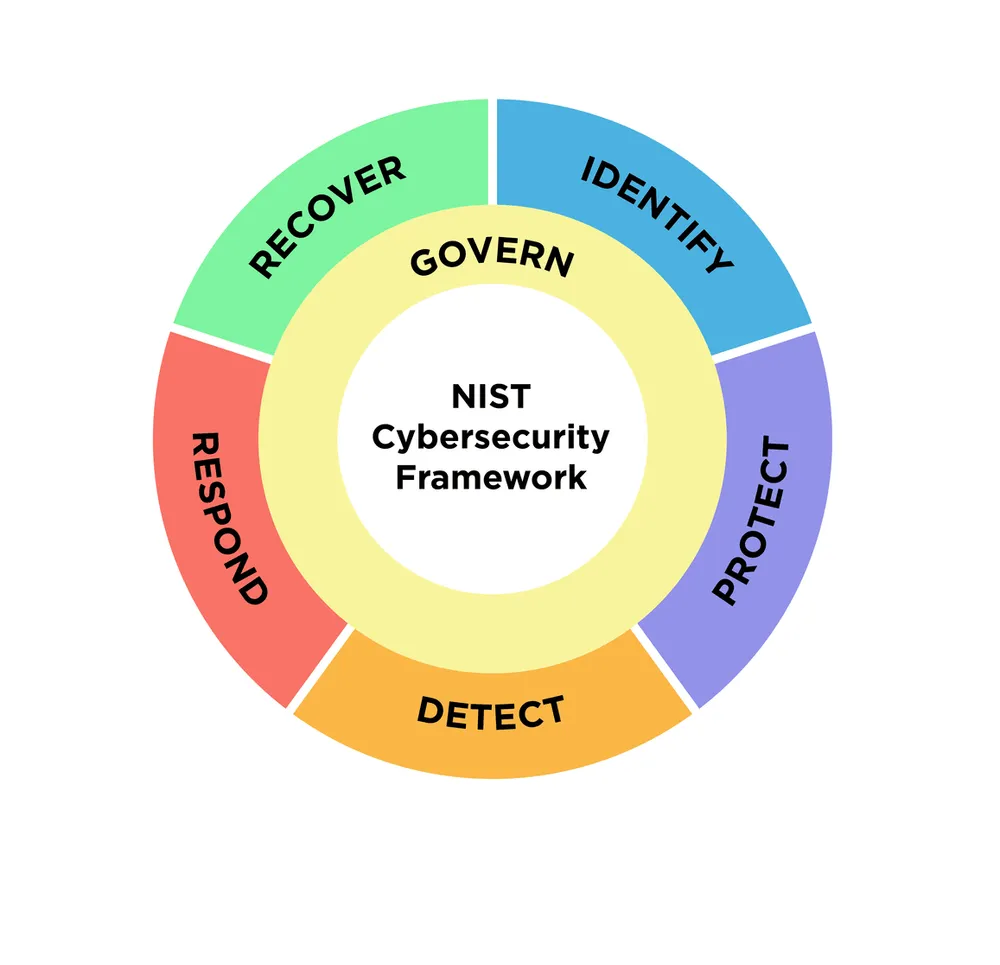
1. The Framework Core: The 5 Functions of a Resilient Program
The Core is the heart of the CSF. It breaks down the entirety of cybersecurity into five simple, continuous functions. Think of them as the five pillars of a well-defended digital kingdom.
- Identify: “Know Your Kingdom.” This is the foundational step. You cannot protect what you don’t know you have. This function includes all the activities required to understand your environment, from maintaining an inventory of all assets (servers, laptops, cloud workloads, data) to conducting risk assessments and establishing governance policies.
- Protect: “Build Your Walls and Train Your Guards.” This function encompasses the safeguards you implement to prevent a cybersecurity event from happening. It includes access control (IAM), employee awareness training, data security (encryption), and protective technologies like firewalls and endpoint protection.
- Detect: “Set Your Watchmen on the Walls.” No defense is perfect. This function is about implementing measures to identify a cybersecurity event in real-time. It includes continuous monitoring, anomaly detection, and analyzing logs and network traffic for signs of malicious activity.
- Respond: “Sound the Alarm and Fight the Battle.” When a breach is detected, what do you do? This function covers the activities required to take action once an incident is identified. It includes response planning, communication with stakeholders, analysis, mitigation, and improvements.
- Recover: “Rebuild and Learn.” After the battle is over, how do you get back to normal? This function focuses on restoring capabilities and services that were impaired during an incident. It includes recovery planning, improvements to your strategy, and communications to rebuild trust.
Each of these Functions is broken down into Categories (e.g., Asset Management) and Subcategories (e.g., “Physical devices and systems within the organization are inventoried”), which are the specific desired outcomes.
2. The Implementation Tiers: Gauging Your Cybersecurity Maturity
The Tiers describe how mature and sophisticated an organization’s cybersecurity risk management practices are. They provide a way to measure your progress from a reactive stance to a proactive and adaptive one.
- Tier 1: Partial - Cybersecurity is ad-hoc, reactive, and often chaotic. There is limited awareness of risk, and processes are informal.
- Tier 2: Risk-Informed - There is a formal risk management process in place, but it may not be applied consistently across the entire organization.
- Tier 3: Repeatable - The organization has a formal, documented, and consistently applied risk management process. Policies and procedures are well-defined.
- Tier 4: Adaptive - The organization is proactive. It adapts its cybersecurity practices based on lessons learned and predictive indicators.
3. The Framework Profile: Your Roadmap from “Now” to “Next”
This is where the framework becomes a powerful, practical tool. A Profile is a snapshot of your organization’s cybersecurity posture, viewed through the lens of the Framework Core.
- Current Profile: This is your “as-is” state. You go through the Functions, Categories, and Subcategories of the Core and document which outcomes you are currently achieving.
- Target Profile: This is your “to-be” state. Based on your business goals, risk appetite, and regulatory requirements, you define what your ideal cybersecurity posture should look like.
The gap between your Current Profile and your Target Profile is your action plan. It gives you a prioritized, data-driven roadmap for improving your security posture.
The CISO’s Action Plan: How to Implement the NIST CSF in 7 Steps
- Prioritize and Scope: You don’t have to boil the ocean. Decide which part of your business you will focus on first.
- Orient: Identify the systems, assets, regulatory requirements, and overall threat landscape related to the scope you’ve defined.
- Create a Current Profile: With your team, assess your current practices against the Categories and Subcategories of the CSF Core.
- Conduct a Risk Assessment: Analyze your Current Profile in the context of your specific threat landscape to highlight the areas of greatest risk.
- Create a Target Profile: Define your goals and your target state based on the outcomes in the CSF.
- Analyze, Prioritize Gaps, and Create an Action Plan: Identify the gaps between your Current and Target Profiles and prioritize them. This is your strategic roadmap.
- Implement, Measure, and Iterate: Execute your action plan and continuously measure its effectiveness, updating your Current Profile as you improve. The CSF is a living framework.
Beyond the Checklist: The CSF as a Strategic Tool for the CISO
A CISO who masters the NIST CSF has a powerful tool for more than just internal security management.
- Communicating with the Board: The five Functions are a perfect way to communicate with executive leadership in a language they understand. You can translate technical details into a clear business risk narrative.
- Vendor Risk Management: Use the CSF as a common framework to assess the security posture of your key vendors and partners.
- Cloud-Native Adaptation: The CSF is technology-neutral and adapts perfectly to the cloud. The “Identify” function means discovering all your cloud assets. The “Protect” function includes configuring cloud IAM correctly. The framework provides the “what,” and you map it to the “how” using your cloud provider’s tools.
Practical Example: Applying NIST CSF in Action
Here’s a realistic, step-by-step use case that demonstrates how a large organization can leverage the NIST CSF as a strategic, actionable framework not just a checklist.
Use Case: Global Logistics Provider Recovers from Ransomware Attack
Background
A global logistics provider experienced a crippling ransomware attack that halted cargo schedules across multiple continents. Prior to the incident, their security efforts were disjointed and reactive tied only to regulatory checkboxes, not guided by a comprehensive strategy.
Applying the CSF Functions
| NIST CSF Function | Real-World Action | Result / Benefit |
|---|---|---|
| Identify | Discovered that warehouse scanners were running unsupported OS versions an unrecognized asset risk. | Closed a major visibility gap and prioritized security for outdated devices. |
| Protect | Implemented network segmentation and enforced MFA for remote operators, especially crane users. | Reduced attack surface and added strong access controls around critical systems. |
| Detect | Deployed a centralized log analytics platform to monitor lateral movement across the network. | Allowed detection of suspicious behaviors within seconds rather than hours. |
| Respond | Developed a detailed response playbook, defining roles clearly even at port supervisor level and ran containment drills. | Accelerated response times and clarified stakeholder roles in crisis. |
| Recover | Established warm-site failover capabilities and recovery procedures to minimize downtime. | Reduced operational paralysis from days to just hours; restored confidence with insurers and auditors. |
Outcome & Strategic Impact
Within 12 months:
- Insurers lowered cybersecurity premiums.
- Auditors issued clean reports.
- The Board started treating cyber risk with the same rigor as financial risk.
This example isn’t theoretical it’s a powerful demonstration of how the NIST CSF transforms cyber risk from chaos into a structured, measurable, and board-level dialogue. Setting up quarterly heat maps and maturity dashboards helped leadership shift from reactive firefighting to proactive resilience. “Successful adopters secure executive sponsorship early, pilot small for quick wins, and invest in continuous measurement to keep momentum alive.”
Use this case as a blueprint: start with one function or department, prove value quickly, then scale your NIST CSF implementation across the organization.
Conclusion: From Chaos to Clarity
The NIST Cybersecurity Framework is a gift to the overwhelmed security leader. It provides a way to bring structure to the chaos, a common language to bridge the gap between technical and business teams, and a strategic blueprint to guide your security program’s evolution.
Stop thinking of it as a checklist to be completed. Start using it as the powerful communication and management tool it was designed to be. By doing so, you can move your organization toward a more mature, resilient, and adaptive security posture, and you can finally answer the question, “Are we secure?” with data-driven confidence.
To further enhance your cloud security and implement Zero Trust, contact me on LinkedIn Profile or [email protected].
Frequently Asked Questions (FAQ)
What is the difference between the NIST CSF and ISO 27001?
The NIST CSF is a voluntary framework focused on risk management, providing a flexible set of outcomes. ISO 27001 is a formal, certifiable standard specifying requirements for an Information Security Management System ISMS. Many organizations use the CSF as a guide to help them achieve ISO 27001 certification.
Is the NIST CSF mandatory for my organization?
For most private companies, it is voluntary. However, it is considered a standard of care and is mandatory for U.S. federal agencies.
How long does it take to implement the NIST CSF?
Implementation is a continuous journey. Creating an initial Profile can take weeks to months, depending on the scope. The action plan to close the gaps can be a multi-year roadmap.
Is the NIST CSF only for large enterprises?
No. It was designed to be scalable and adaptable for organizations of any size.
Does the NIST CSF apply to cloud security?
Absolutely. The framework is technology-neutral. Its five Core Functions Identify, Protect, Detect, Respond, Recover map perfectly to the challenges of cloud security, such as discovering cloud assets and properly configuring cloud IAM.
Relevant Resource List
- Wiz Academy: The CISO’s NIST Compliance Checklist
- C-Risk Blog: What is the NIST Cybersecurity Framework (CSF)?
- Federal Trade Commission (FTC): Understanding the NIST Cybersecurity Framework
- NIST Cybersecurity Framework Official Website: https://www.nist.gov/cyberframework
