In the rapidly expanding universe of Artificial Intelligence, a new standard is emerging as the central nervous system for AI agents: the Model Context Protocol (MCP). This powerful framework acts as the “valet key” for your AI, allowing your Large Language Models (LLMs) and autonomous agents to securely access the tools and data they need to perform complex tasks. From Claude Desktop to custom internal agents, MCP is becoming the default language for AI collaboration.
But just like a real valet key, if not managed with extreme care, it can be abused. An MCP server, especially one exposed to remote clients, is not just another API it’s a trusted gateway to your organization’s most sensitive data and powerful tools. An insecure MCP server is a backdoor waiting to be discovered.
The recent discovery of critical vulnerabilities like CVE-2025-6514 (a command injection in mcp-remote) has served as a stark wake-up call. The very tools meant to enable AI innovation can become the vector for a full system compromise. The question for every CISO is no longer if they will have MCP servers in their environment, but how they will secure them.
This is the definitive blueprint for securing your remote MCP servers on Google Cloud, moving beyond theoretical best practices to a practical, defense-in-depth architecture.
The Threat Model: Why Your MCP Server is a High-Value Target
Before architecting a defense, we must understand the attacker’s perspective. A remote MCP server is a uniquely attractive target because it is designed to be a trusted broker. Compromising it allows an attacker to:
- Hijack AI Agents: An attacker can manipulate the MCP server to send malicious instructions to connected AI agents, turning them into insider threats.
- Poison Tools and Data: By compromising the server, an attacker can poison the tools and data sources that your AI relies on, subtly corrupting its outputs and decisions.
- Execute Commands: As seen with CVE-2025-6514, flaws in the server or its connected clients can allow for direct Remote Code Execution (RCE).
- Bypass Existing Controls: An attacker who compromises the MCP server can often inherit the trust and permissions granted to it, bypassing traditional network and identity controls.
The core challenge is that many MCP server implementations are being deployed by AI developers who may not be seasoned security or API experts, often leading to classic web vulnerabilities in this new, high-stakes context.
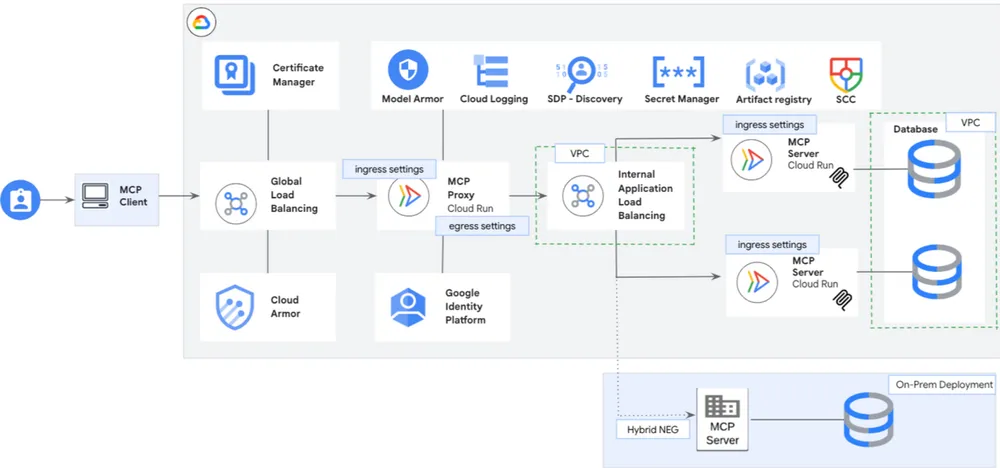
The Google Cloud Blueprint: A Multi-Layered Defense for Your MCP Server
Securing a remote MCP server is not about a single product; it’s about building a layered, resilient architecture. Here is a practical, step-by-step guide using Google Cloud’s native security services.
Layer 1: The Foundation A Secure and Isolated Network
Your first line of defense is to ensure the MCP server doesn’t run in a wide-open, default network.
- Action: Deploy your MCP server (e.g., on a Google Compute Engine VM or a GKE cluster) within a dedicated Virtual Private Cloud (VPC).
- VPC Firewall Rules: Implement strict, “default-deny” firewall rules. Do not allow ingress from
0.0.0.0/0. Explicitly allow traffic only from the specific IP ranges of your trusted clients or from Google’s own infrastructure (like the IAP service, which we’ll cover next).
Layer 2: The Unbreakable Front Door Identity-Aware Proxy (IAP)
This is the cornerstone of a Zero Trust architecture for your MCP server. Do not expose your server directly to the internet. Identity-Aware Proxy (IAP) is a fully managed service that acts as a secure, identity-verifying gateway for your application.
- Action: Place your MCP server behind a Google Cloud Load Balancer and enable IAP.
- How it Works: When a client tries to connect to your MCP server, the request hits IAP first. IAP completely blocks the request until it has verified two things:
- Authentication: It forces the user or client to authenticate with their Google Identity (or federated identity).
- Authorization: It checks your IAM policy to ensure that this specific identity has been granted the
IAP-secured Web App Userrole for your MCP server.
- The Benefit: This single step eliminates unauthenticated access. An attacker scanning the internet will not even be able to see your MCP server’s login page, let alone send malicious requests to it. You have moved your security perimeter from the network layer to the identity layer.
Layer 3: The Edge Shield Cloud Armor
Even with IAP handling authentication, your MCP server is still a web-facing application and needs protection from broad, internet-based threats.
- Action: Attach a Google Cloud Armor security policy to the same load balancer that is fronting your MCP server.
- How it Works: Cloud Armor provides two critical functions at the edge of Google’s network:
- DDoS Protection: It automatically absorbs massive Layer 3/4 and Layer 7 Distributed Denial-of-Service attacks, ensuring the availability of your MCP server.
- Web Application Firewall (WAF): You can apply managed WAF rules (like the OWASP Top 10) to block common web exploits like SQL injection or cross-site scripting before they ever reach your server. You can also implement geo-based blocking to restrict access from high-risk regions.
Layer 4: The Secure Transit End-to-End Encryption
Unsecured HTTP is not an option. All communication between your MCP clients and the server must be encrypted.
- Action: Configure your Google Cloud Load Balancer with a Google-managed SSL certificate.
- The Benefit: This provides robust, automatically renewed TLS encryption for all traffic in transit, protecting the confidentiality and integrity of the data being exchanged between your clients and the MCP server.
Layer 5: The Secure Runtime The Principle of Least Privilege
Your MCP server application itself should not run with excessive permissions.
- Action: Create a dedicated, single-purpose IAM service account for your MCP server. Grant this service account only the absolute minimum set of permissions it needs to perform its specific tasks (e.g., accessing a specific Cloud Storage bucket or a BigQuery dataset).
- The Benefit: Do not use the default Compute Engine service account, which often has the overly permissive “Editor” role. By using a least-privilege service account, you drastically limit the “blast radius” if your application code itself is ever compromised. The attacker will only have access to the limited permissions of the dedicated service account, not the entire project.
Layer 6: The Watchtower Continuous Monitoring and Logging
You must have visibility into who is accessing your MCP server and what they are doing.
- Action: Enable and regularly review Cloud Audit Logs and the logs from your IAP and Cloud Armor services.
- How it Works:
- IAP Logs: Provide a detailed audit trail of every access request who was granted access, who was denied, from where, and at what time.
- Cloud Armor Logs: Show you all the traffic that was blocked by your WAF rules.
- Cloud Audit Logs: Record all the API calls made by the MCP server’s service account.
- The Benefit: This rich telemetry, especially when fed into a platform like Chronicle Security Operations, allows you to create high-fidelity alerts for anomalous behavior, conduct effective threat hunting, and perform deep forensic analysis during an incident.
Conclusion: Building the Secure Foundation for the Agentic Era
The Model Context Protocol is a transformative technology that will unlock the next wave of AI innovation. But with great power comes great responsibility. Deploying a remote MCP server is not a casual act; it’s the creation of a new, highly sensitive piece of your enterprise infrastructure.
A “build it fast and secure it later” approach is a recipe for disaster. By leveraging the integrated, defense-in-depth security controls of Google Cloud from the network isolation of VPCs and the edge protection of Cloud Armor, to the powerful Zero Trust enforcement of IAP and the granular control of IAM you can build a secure, resilient, and trustworthy foundation for your AI agents. This is how you enable your organization to confidently step into the agentic era.
To further enhance your cloud security and implement Zero Trust, contact me on LinkedIn Profile or [email protected].
Frequently Asked Questions (FAQ)
What is the single most important step to secure a remote MCP server on GCP?
The single most critical step is to place it behind the **Identity-Aware Proxy IAP**. This enforces strong, identity-based authentication for every connection and ensures that your server is completely invisible to unauthenticated users on the internet.
Why is using a dedicated, least-privilege service account so important?
It adheres to the principle of least privilege and dramatically limits the "blast radius" of a potential compromise. If an attacker exploits a vulnerability in your MCP server's application code, they will only gain the minimal permissions assigned to that dedicated service account, not broad control over your entire GCP project.
Do I need Cloud Armor if I'm already using IAP?
Yes. They serve two different, complementary purposes. IAP is an **authentication and authorization** gateway verifying *who* you are. Cloud Armor is a **WAF and DDoS protection** service blocking *what* you're trying to do if it's malicious. You need both for a defense-in-depth architecture.
How do I protect against vulnerabilities like CVE-2025-6514 in my client tools?
While the server-side controls outlined here provide a robust defense, client-side security is also essential. You must keep your client-side tools like `mcp-remote` or the Claude Desktop patched and up-to-date. The server-side IAP would, in many cases, block the initial unauthenticated connection attempt from an exploited client.
Is it safe to expose an MCP server to the internet?
It is only safe if you do it correctly. Exposing it directly on a VM with a public IP is extremely risky. However, exposing it through the layered architecture described here fronted by a Google Cloud Load Balancer with Cloud Armor and IAP is a secure and robust architectural pattern.
