
The world of AI development is moving at breakneck speed, with new tools and protocols emerging to create increasingly powerful and autonomous AI agents. One of the most significant of these is Anthropic’s Model Context Protocol (MCP), an open standard designed to be the connective tissue for Large Language Model (LLM) applications. However, this rapid innovation brings new attack surfaces, a fact laid bare by the discovery of a critical security vulnerability in Anthropic’s MCP Inspector developer tool.
Tracked as CVE-2025-49596, this vulnerability carries a severe CVSS score of 9.4 out of 10.0 and enables Remote Code Execution (RCE) on a developer’s machine. An attacker could exploit this flaw to steal data, install backdoors, and move laterally across networks, posing a serious risk to AI teams, open-source projects, and enterprises relying on the MCP ecosystem. This isn’t just another bug; as Oligo Security noted in their report, it represents “a new class of browser-based attacks against AI developer tools,” and it serves as a critical wake-up call for the entire industry.
What is the Model Context Protocol (MCP) and the MCP Inspector?
Introduced in late 2024, the Model Context Protocol (MCP) standardizes how LLM applications integrate and share data with external tools and data sources. It provides a framework for AI agents to interact with their environment in a structured way.
To help developers build on this protocol, Anthropic provided the MCP Inspector, a developer tool for testing and debugging MCP servers. It consists of two main components:
- A client: A web-based user interface for testing and debugging.
- A proxy server: A bridge that connects the web UI to various MCP servers.
The critical security consideration, as noted in the tool’s documentation, is that the proxy server has permission to spawn local processes and should never be exposed to an untrusted network. Unfortunately, as researchers found, default configurations and a chain of browser-based vulnerabilities can violate this core principle with alarming ease.
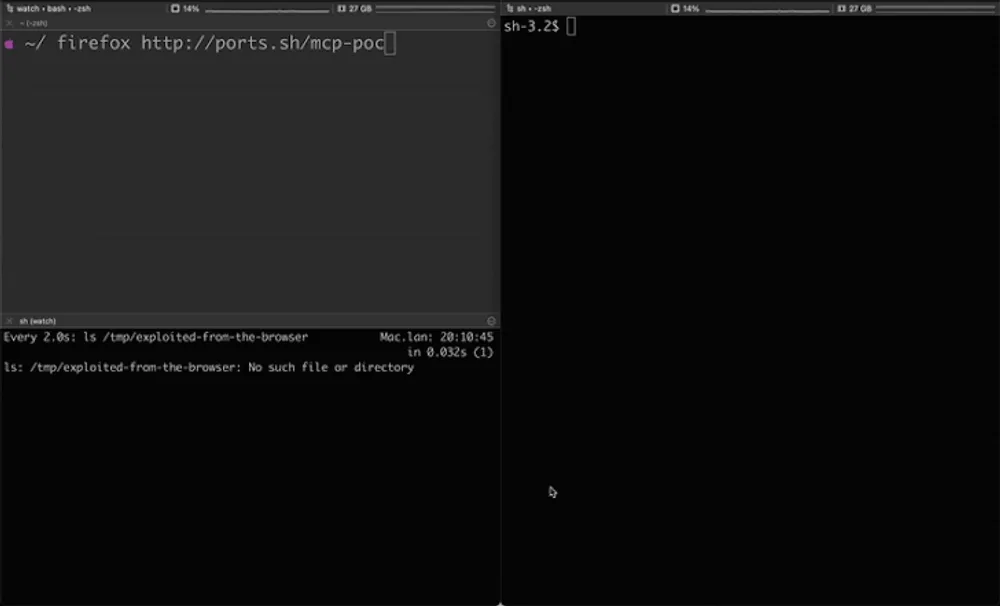
The Attack Chain: How a Website Visit Leads to RCE
The exploit is not a single flaw but a clever chaining of multiple vulnerabilities a classic case of how seemingly minor issues can combine to create a critical threat.
1. The Insecure Default: A Server Open to the World
The first link in the chain is a common developer misconfiguration. When developers spin up a local MCP Inspector for testing, the default settings often bind the server to the IP address 0.0.0.0. Unlike 127.0.0.1 (localhost), which only accepts connections from the machine itself, 0.0.0.0 tells the operating system to listen for connections on all network interfaces.
As Oligo Security pointed out, “This misconfiguration creates a significant attack surface, as anyone with access to the local network or public internet can potentially interact with and exploit these servers.” It’s like leaving your front door unlocked and open to the street.
2. The Browser Flaw: The “0.0.0.0 Day” Exploit
The second link is a 19-year-old logical vulnerability in modern web browsers dubbed “0.0.0.0 Day.” Browsers often fail to handle the 0.0.0.0 address securely. This means a malicious script running on an external website can send requests to http://0.0.0.0:[port], and the browser will route this request to the corresponding service running on the victim’s local machine. This effectively bypasses network boundaries that are meant to keep localhost services isolated.
3. The Missing Lock: CSRF in the MCP Inspector (CVE-2025-49596)
The final link is the vulnerability itself. Per the CVE description and research, versions of MCP Inspector below 0.14.1 lacked authentication between the client and the proxy. This is a classic “Missing Authentication for Critical Function” (CWE-306) weakness.
This flaw allows unauthenticated requests to launch MCP commands over stdio (standard input/output), creating a perfect setup for a Cross-Site Request Forgery (CSRF) attack.
Putting It All Together: The Attack Scenario
Here’s how an attacker could chain these flaws to achieve RCE:
- The Lure: An attacker crafts a malicious website and tricks a developer (who is running a vulnerable MCP Inspector locally) into visiting it.
- The Attack: Malicious JavaScript embedded in the website sends a carefully crafted request to
http://0.0.0.0:6277(the default MCP Inspector proxy port). This request might use the Server-Sent Events (SSE) endpoint to dispatch a command. - The Compromise: Due to the “0.0.0.0 Day” flaw, the browser forwards this request to the developer’s local machine. Because of CVE-2025-49596, the MCP Inspector proxy accepts and executes the unauthenticated command, leading to arbitrary code execution on the developer’s host machine.
Attackers could also leverage DNS rebinding techniques to achieve the same result, making this a versatile and dangerous attack vector.
The Ripple Effect: MCP Security is an Ecosystem Problem
This vulnerability’s discovery comes amidst a growing conversation about the security of the broader AI agent ecosystem.
- Context Poisoning and Prompt Injection: As noted by Trend Micro, other vulnerabilities like SQL injection bugs in MCP servers can be used to “seed” malicious prompts into databases. When an AI agent later pulls this “trusted” data, it can be influenced to execute malicious commands or exfiltrate data.
- The “NeighborJack” Vulnerability: Research from Backslash Security found hundreds of MCP servers susceptible to misconfigurations that allowed arbitrary command execution and made them accessible to anyone on the same local network (e.g., a coffee shop Wi-Fi). As they put it, “It’s like leaving your laptop open – and unlocked for everyone in the room.”
These findings highlight a clear and present danger: if we allow yesterday’s web-app mistakes to slip into today’s agent infrastructure, we gift attackers an effortless path to full agent compromise.
The Fix and the Path Forward
Following responsible disclosure from Oligo Security, the MCP Inspector project maintainers at Anthropic addressed CVE-2025-49596 with the release of version 0.14.1 on June 13, 2025.
The Fix Includes:
- Session Tokens: The proxy server now requires a session token for authentication, preventing unauthenticated requests.
- Origin Validation: The server now verifies the
HostandOriginheaders in HTTP requests, ensuring it is only communicating with known, trusted domains and blocking CSRF and DNS rebinding attacks by default.
For developers and organizations, the path forward is clear:
- Upgrade Immediately: Anyone using Anthropic’s MCP Inspector should upgrade to version 0.14.1 or later. You can check your version with
npm list -g @modelcontextprotocol/inspector. - Adopt a Skeptical Mindset: Treat local developer tools with the same security scrutiny as production services. Avoid binding to 0.0.0.0 unless absolutely necessary and properly firewalled.
- Secure the Ecosystem: As Backslash Security noted, the long-term solution involves building AI clients and agents that are “skeptical and aware of the threat posed by context poisoning,” using AI rules and predefined prompts to guide their behavior safely.
Conclusion: Securing the Foundation of the Agentic Age
The discovery of CVE-2025-49596 is more than just a patch note; it’s a critical lesson for the nascent AI development ecosystem. It proves that the very tools built to accelerate innovation can become powerful attack vectors if fundamental security principles like authentication and secure-by-default configurations are overlooked. As AI agents, powered by protocols like MCP, become more autonomous and integrated into our digital lives, securing them is not just an option it is the foundation upon which this entire new era of technology must be built. The industry must move forward with a security-first approach, ensuring that the next wave of AI is not only powerful but also trustworthy and resilient.
To further enhance your cloud security and implement Zero Trust, contact me on LinkedIn Profile or [email protected].
Frequently Asked Questions (FAQ)
What is CVE-2025-49596?
It is a critical vulnerability CVSS score 9.4 in Anthropic's MCP Inspector tool versions below 0.14.1 that allows for Remote Code Execution RCE on a developer's machine due to a lack of authentication.
How does the attack work?
It chains together three issues: 1) an insecure default configuration where the MCP server listens on all network interfaces 0.0.0.0, 2) a browser flaw ("0.0.0.0 Day") that allows external websites to send requests to local services, and 3) the lack of authentication (CSRF vulnerability) in the MCP Inspector itself, allowing it to execute arbitrary commands sent from a malicious website.
Who is affected by this vulnerability?
AI developers and organizations using vulnerable versions of Anthropic's MCP Inspector tool below 0.14.1 are affected. This includes users of open-source projects that may depend on the tool.
How do I fix this vulnerability?
You must upgrade to MCP Inspector version 0.14.1 or later. You can do this by running the command: `npm install -g "@modelcontextprotocol/inspector@^0.14.1"`.
What is the Model Context Protocol (MCP)?
MCP is an open protocol, introduced by Anthropic, that standardizes how AI applications and agents interact with external tools and data sources, forming a key part of the modern AI ecosystem.
Relevant Resource List:
- The Hacker News: “Critical Vulnerability in Anthropic’s MCP Exposes Developer Machines to Remote Exploits”
- Oligo Security Blog: “CVE-2025-49596: RCE in MCP-Inspector” (Technical deep-dive from the researchers)
- NVD: “CVE-2025-49596 Detail”
- GitHub Advisory: GHSA-7f8r-222p-6f5g
